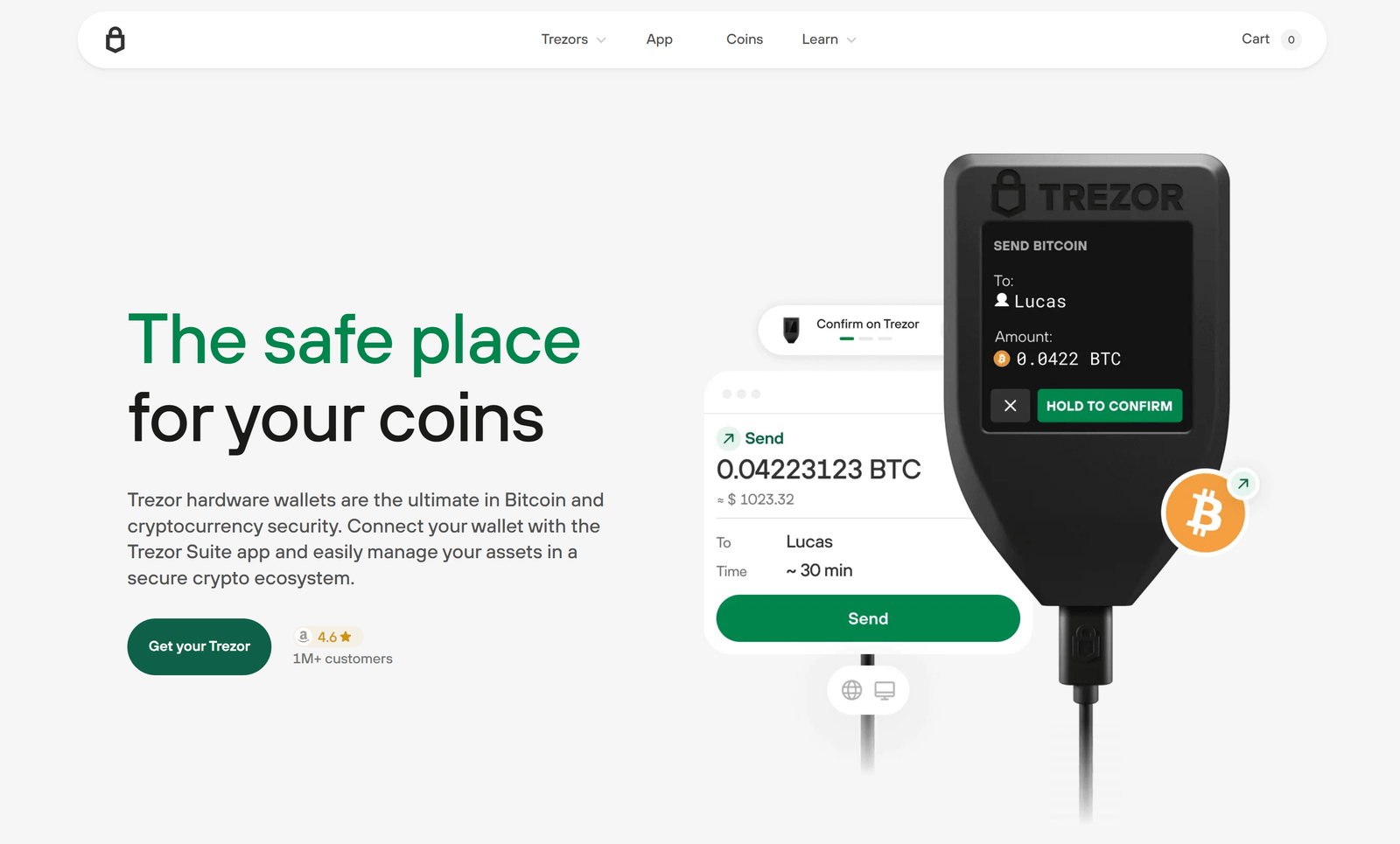
Login model — hardware first
Trezor’s login model intentionally rejects centralized credentials. Access is established by physically connecting and operating your Trezor device. The host application or browser orchestrates account discovery and transaction proposals, but signing authority remains with the hardware. This ensures that secrets never transit or persist on the host machine, and every sensitive action requires manual confirmation on the device’s screen.
Getting started: safe connection and verification
Begin by using official resources to obtain the required companion software such as Trezor Suite or Trezor Bridge when applicable. Connect your device via USB (or supported transport) and follow on-screen prompts. During initial setup you will create a PIN and record your recovery seed directly on the device. These credentials must be kept offline and private — never enter them on a computer or website.
Note: always confirm device authenticity and installed firmware when prompted; unexpected prompts or unusual messages should be treated with caution.
How a Trezor login session functions
When a login or signing operation is requested, the host constructs a request and Bridge/Suite forwards it to the device. The Trezor displays human-readable details — addresses, amounts, contract parameters — which you must verify before approving. Only after your explicit on-device confirmation will the Trezor produce a cryptographic signature and return it to the host.
Recommended security practices
- Download official software only from trezor.io/start and verify signatures when available.
- Record and store your recovery seed offline in multiple secure locations; consider metal backups for long-term durability.
- Never enter or transmit your seed or private keys to any online service, email, or chat.
- Confirm transaction details on the device display before approving.
- Keep firmware and companion software up to date; install updates only via official tooling.
- Use a trusted host for high-value operations and minimize browser extensions that could interfere with wallet flows.
Privacy considerations
Trezor transmits only the public data required to display accounts and build transactions. For users concerned with network privacy, consider using network protections such as Tor, VPNs, or dedicated privacy nodes in conjunction with the host application. Limit telemetry in application settings where offered, and use coin-control features to reduce address reuse when privacy is a priority.
Troubleshooting common login issues
Typical connectivity problems are resolved by simple checks: ensure the device is unlocked and on the home screen, try a different USB cable or port (prefer direct ports over hubs), restart the host application, and confirm any required Bridge/Suite helper is running. If issues persist, consult official documentation and support resources rather than unverified guides.
Conclusion
Trezor Login is built to place control and verification in the hands of the user. By relying on on-device confirmations, hardware-stored keys, and verified software sources, the Trezor login model dramatically reduces attack surface and supports robust self-custody practices. Follow official guidance, secure your recovery seed, and always verify on-device details to maintain the highest security posture.